
Expel
Expel for Microsoft: Security monitoring and detection for Defender, Azure, and Office 365
3 years ago - 3:57

CS3STHLM
Erik Hjelmvik - TLS Interception and Decryption
5 years ago - 38:50

Cisco DevNet
Using Cisco pxGrid for Security Platform Integration
8 years ago - 40:04

Expel
Maximize your existing SIEM investment
1 year ago - 1:38

AWS Events
AWS re:Inforce 2022 - How to implement more effective security monitoring for AWS (DEM222-S)
2 years ago - 12:27

Expel
How Expel makes onboarding unexpectedly simple
3 years ago - 0:57

Hacker Zone
lateral movement | Lateral Movement with Local Administrator | Red Teaming | Privilege Escalation
3 months ago - 9:38

dev.010
Splunk Log Analysis: Detecting New User Creation via AtomicRedTeam Test
5 months ago - 2:26

TheDevOpsSchool
Splunk Fundamental Tutorial By Piyush - 2020 -
5 years ago - 1:54:57

AWS Events
AWS re:Inforce 2024 - Securing the software supply chain with detection as code (TDR224-S)
1 year ago - 18:34

AtlanticCouncil
ESIS: AI-based monitoring for securing industrial IoT and the energy transition from cyberattacks
Streamed 3 years ago - 31:34

BlueSky Citadel
INTRODUCTION TO CYBER SECURITY SEC101 | BlueSky Citadel
8 months ago - 1:44:16

SecurityFirstCorp
What Are the Key Responsibilities of a Security Engineer? | SecurityFirstCorp News
6 months ago - 3:30

AWS Events
AWS re:Inforce 2023 - Secure the software supply chain w/ detection as code & modern SIEM (PRT210-S)
2 years ago - 14:28

Group-IB
Group-IB DFIR team: forensic examination of incidents involving source code leaks
4 years ago - 0:37

Gary Berman
"Security Operations Centers: Unpacked"
Streamed 4 years ago - 47:22

BlueSky Citadel
INTRODUCTION TO CYBERSECURITY SEC101 - CLASS1 | BlueSky Citadel
8 months ago - 1:27:59

Expel
Expel managed phishing: Investigation and response for your phishing inbox
3 years ago - 2:18

IT Visionaries
Analyzing the ‘Top Data Security Trends for 2022’ With Dave Merkel Co-founder and CEO, Expel
2 years ago - 4:49

Datadog
Bits of Security, Expel: db.topics.insertOne({name:"Database observability for security purposes"})
4 years ago - 32:16

Expel
Simplifying your multi-cloud security with Expel
1 year ago - 2:24

BAKOTECH
Threat Detection & Incident Response for the Hybrid Infrastructures
Streamed 4 years ago - 50:49

ChannelBytes
What’s the difference between an MDR and a EDR vendor?
3 years ago - 2:58

Expel
What does Expel response look like? (a demo)
3 years ago - 2:12

Eclypsium
Protecting the Exposed Network Edge from APTs, Zero Days and Ransomware
3 weeks ago - 59:38

BytesTechnology
Examining the Cyber-security Threat Landscape with Sophos
3 years ago - 49:09
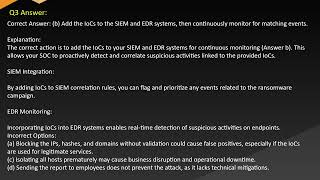
Certbie
ECCouncil Exams 312 39 Certified SOC Analyst Free Practice Questions Updated
10 days ago - 53:22

Anton Chuvakin
EP154 Mike Schiffman: from Blueboxing to LLMs via Network Security at Google
1 year ago - 35:41

Anton Chuvakin
EP154 Mike Schiffman: from Blueboxing to LLMs via Network Security at Google | Cloud Security...
1 year ago - 35:41

Expel
Expel for Email: Protect against business email compromise
3 years ago - 0:45

ETDA Thailand
“Thailand Cybersecurity Week 2017” 30-06-2017_3"Mohd Zabri Adil Talib "
Streamed 7 years ago - 1:27:55

Expel
Expel Detection Day (Monitoring Microsoft): How to use Defender to investigate a ransomware incident
3 years ago - 45:07

Certdemy
CCNA Security Cisco Certified Network Associate Security Exam Free Practice Questions
1 year ago - 1:06:24





































