
EthicalHackerCommunity
@ethicalhackercommunity1710 subscribers

Ethical hacker community
@ethicalhackercommunity3078 subscribers

Null:404 Cyber Security
Hackers, learners, cybersec enthusiasts! 🛡️ Meet us where we're at - Null404 has you covered across all platforms. We gather ...
@null404cybersec subscribers

Hacking = Freedom
How To Become An Ethical Hacker! #ethicalhacker #howtobecomeahacker #ethicalhacking #cybersecurity
10 months ago - 0:30

The Dark Net
How Ethical Hackers Make Money! #cybersecurity #ethicalhacking #hackers #computer #tech #infosec
3 months ago - 0:51

Ethical Hacker
Welcome to Ethical Hacker - Your Gateway to Ethical Hacking!
11 months ago - 1:09

Intigriti
Intigriti Customer Story: MuuseLabs protects children’s IoT devices through ethical hacking
5 years ago - 2:53

XploitGhost
A real hacker should know about this
6 months ago - 0:20

noisytech13
Ethical Hacking 101: Your Ultimate Introduction to the World of White Hat Hacking
1 year ago - 3:06

Cyber Defend X
Master Ethical Hacking Free Series in 2024 | Learn Oscp and Osint Tools | Owasp & Windows Security
1 year ago - 7:47

Iheb Hamad
Constructing Bug Bounty Methodology: Episode 2 - Mastering Passive Reconnaissance Tools
1 year ago - 22:10

Detectify
EASM: Is it late to the party?
3 years ago - 3:02

Craw Academy
ChatGPT can assist with ethical hacking in a number of ways including: #chatgpt #hacking #shorts
1 year ago - 0:16

HackerOne
Trusted and Vetted
11 months ago - 2:44

Intigriti
Intigriti Customer Story: Combell tests infrastructure security with the help of ethical hackers.
4 years ago - 2:49

Ethical Hackers
@EthicalHackers-jy2ip subscribers

Open Royalty
Regarding learning 5 Linux Command #2
2 years ago - 2:58

Internet Society On-Demand
LIVESTREAM: From Villains to Heroes: The Hacking Evolution @awsstartups @michielprins...
7 months ago - 1:05:47

Innovative Insight
Lecture 1.7| Installation and Working of Nmap Scanner | Cyber Security Course | Hindi & Urdu
1 year ago - 11:52

BSidesCharm
BSidesCharm 2022 - Extortion, Chaos and Needless Busywork AKA Vendor Risk Management
3 years ago - 53:08

Open Royalty
Regarding learning 3 Linux TERMINAL
2 years ago - 1:57

Open Royalty
About the Learning Section - HTTP Protocol
2 years ago - 1:56

Open Royalty
DHCP - Dynamic Host Configuration Protocol
2 years ago - 2:02

Open Royalty
About the Learning Section - 4 Changing Network Information
2 years ago - 4:32

Open Royalty
About the Learning Section - 5 Fake Authentication Attack
2 years ago - 7:02

Open Royalty
Part 1 How to Install Linux for Beginners
2 years ago - 1:01

Open Royalty
Learning Section - Attacking Server
2 years ago - 8:50

Open Royalty
Regarding learning 4 Tor Browser
2 years ago - 3:39
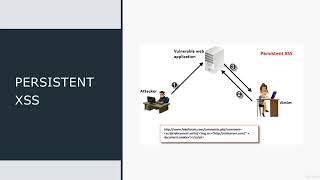
Open Royalty
Learning Section - Cross Site Scripting XSS
2 years ago - 3:00

Open Royalty
Regarding learning 1 Anonymous
2 years ago - 0:54

Bug Bounty University
Hunting on Site A, Finding Bugs on Site B - Bug Bounty PoC | Bug Bounty University
2 years ago - 1:04

Intigriti
Intigriti Client Testimonial: Telenet and UZ Leuven
5 years ago - 2:49

Open Royalty
How to Install Linux for Beginners
2 years ago - 6:57

Open Royalty
Learning Section - Server Hacking
2 years ago - 6:26

Open Royalty
Learning Section - Command Execution Attack
2 years ago - 9:24

Open Royalty
About the Learning Section - 3 Capturing Packets
2 years ago - 4:51

Open Royalty
Regarding learning 1 Kali Linux
2 years ago - 0:43

Secrets
How Two Kids Brought the CIA to Its Knees
1 month ago - 10:37

Open Royalty
What's that Internet Tracking
2 years ago - 2:31

Open Royalty
Learning Section - Injection Flaw
2 years ago - 1:54

Open Royalty
Learning Section - Metacharacters
2 years ago - 3:46

Open Royalty
About the Learning Section - 2 WiFi card mode
2 years ago - 4:50

Open Royalty
What's that Internet Protocol Address
2 years ago - 8:21

Open Royalty
Regarding learning 7 Linux Command #4
2 years ago - 4:12

Open Royalty
About the Learning Section - 1 WEP Wired Equivalent Privacy
2 years ago - 3:09

NSConclave
Pentester's Mindset! - @_RaviRamesh
5 years ago - 30:38

Open Royalty
Regarding learning 6 Linux Command #3
2 years ago - 2:15

Iheb Hamad
Constructing Bug Bounty Methodology: Episode 2 - Mastering Passive Reconnaissance Tools
1 year ago - 22:10

Open Royalty
About the Learning Section - 1 Basics
2 years ago - 1:41

Open Royalty
About the Learning Section - 4 WEP Cracking
2 years ago - 4:30

Cyber Defend X
Master Ethical Hacking Free Series in 2024 | Learn Oscp and Osint Tools | Owasp & Windows Security
1 year ago - 7:47

Open Royalty
Command Execution Advance Attack
2 years ago - 4:01

Open Royalty
About the Learning Section - Request header
2 years ago - 4:09

Detectify
What are organizations doing wrong when it comes to security?
3 years ago - 3:54

Open Royalty
About the Learning Section - 7 Advance capturing
2 years ago - 6:36

Open Royalty
About the Learning Section - 2 Analyzing Network
2 years ago - 5:05

Yash Kanani
2FA Bypass | How to Bypass OTP with Burp Suite| Yash Kanani | #bugbounty #ethicalhacking #youtube
9 months ago - 8:53

Open Royalty
About the Learning Section - HTTP Method
2 years ago - 3:30

Craw Academy
ChatGPT can assist with ethical hacking in a number of ways including: #chatgpt #hacking #shorts
1 year ago - 0:16

Open Royalty
About the Learning Section - 6 ARP
2 years ago - 7:24

Open Royalty
NAT - Network Address Translation
2 years ago - 4:47

Open Royalty
About Learning Section - Information Gathering Whois record
2 years ago - 6:07

Open Royalty
About the Learning Section - Response header
2 years ago - 3:46

Open Royalty
Dmitry - About Learning Section - Information Gathering Dmitry
2 years ago - 6:29

Detectify
Understanding pentesting vs an automated hacker-powered tool
3 years ago - 2:41








































































