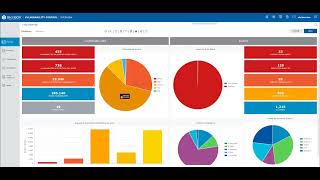
vMiss
All About CISA Known Exploited Vulnerabilities (CISA KEV Catalog)
2 years ago - 5:34

Nucleus Security
Using CISA KEV for Vulnerability Management
2 years ago - 11:36

SecPod
Managing CISA KEV (Known Exploitable Vulnerabilities) using CVEM
10 months ago - 1:07:08

Phoenix Security
🚨Critical Cisco #Zero-Day #Vulnerability #CVE-2023-20198 Explained 🚨#CISAKEV #mitigation detection
1 year ago - 4:13

Tanium
Comply - SBOM, CISA KEV, Exception Management - Tanium Tech Talks #71
1 year ago - 35:36

Nucleus Security
CISA KEV (Known Exploitability Vulnerabilities) Nucleus Product Demo
2 years ago - 3:57

Phoenix Security
Discover the truth behind #cisa #kev #vulnerability with cyber risk #visualization #ransomware
1 year ago - 3:14

Phoenix Security
Unveiling Top #Ransomware #Targets in #Tech Industry #cisa #kev Are You at Risk?
1 year ago - 0:54

BSidesLV
GF - Discover the Hidden Vulnerability Intelligence within CISA's KEV Catalog
10 months ago - 22:00

VulnCheck
Webinar: Exploring Vulnerability Exploitation Beyond CISA KEV
1 year ago - 52:12

Securin Inc
CISA KEV | Vice Society | LV Ransomware | Cyber Threat Intelligence | Podcast
2 years ago - 7:15

Securin Inc
LockerGoga | Bitlocker | CISA KEV catalog | Cyber Threat Intelligence | Podcast
2 years ago - 6:04

Securin Inc
Lazarus | CISA KEV | Water Labbu | Cyber Threat Intelligence | Podcast
2 years ago - 4:56

IT SPARC Cast
Actively Exploited: Broadcom & Commvault Vulnerabilities Added to CISA KEV List
1 month ago - 7:38

Securin Inc
APT29 | APT41 | CISA KEV catalog | Cyber Threat Intelligence | Podcast
2 years ago - 5:44

Tanium
#vulnerabilitymanagement with #cisa #kev & #Tanium #informationsecurity #riskmanagement #shorts
1 year ago - 0:26

Securin Inc
Cuba Ransomware | Maui Ransomware | CISA Kev | Top cyber threats of the week | Podcast
2 years ago - 5:13

VulnCheck
Exploring VulnCheck KEV and CISA KEV w/ Jupyter Notebooks
7 months ago - 14:53

Phoenix Security
NEW #CISA 🔒 #KEV #Ransomware #Alert: #Must-Know #Vulnerabilities & Remediation #cybersecurity
1 year ago - 2:06

CISO Series
DOGE outrage and lawsuit, CISA KEV additions, DeepSeek encryption lapses
5 months ago - 9:03

Secure Thread
CVE-2025-24054 | New NTLM Vulnerability Exploited in the Wild
2 months ago - 0:11

Info Ninja
3 Critical Vulnerabilities in Windows & Zyxel Devices: 2025 Update
5 months ago - 1:17

Phoenix Security
Unleashing the #Power of #vulnerability #data to Tackle #Risk reduction #cybersecurity
1 year ago - 0:44

ComplianceCow
“Evolving GRC into a Real-Time Risk Intelligence Engine.”
2 months ago - 1:26

Glass of 0J
Glass of 0J CISA Known Exploited Vulnerabilities
3 years ago - 15:08

Phoenix Security
Mastering #Cybersecurity #Automating Information for Maximum Protection #appsec
1 year ago - 0:53

Phoenix Security
#Differences Between #AppSec and #SCA #opensource #vulnerability Scanners #cybersecurity
1 year ago - 0:38

Phoenix Security
Unlocking #Business #Success #Fixing #Broken #Processes for LongTerm Benefits #cyber
1 year ago - 0:52

Phoenix Security
Unveiling the Power of Social Media DataAnalysis #epss #kev #cybersecurity #vulnerabilitymanagement
1 year ago - 0:34

BclarkCodes
Recent Cyber Threats and Scams (April 28-May 1, 2025) | A.I. Podcast
2 months ago - 26:28

Phoenix Security
Cracking the Code Unveiling the #Top #Vulnerabilities in #Cybersecurity #vulnerabilitymanagement
1 year ago - 0:45

Phoenix Security
TOP #Exploited #Vulnerabilities in 2023/24 #CISA Vulnerabilities Analysis! 🚨 Must Know Insights! 📊
7 months ago - 3:09
Phoenix Security
Gamechanging Strategy to #Eliminate #99.99 #Vulnerabilities #priority #vulnerabilitymanagement
1 year ago - 0:40

Help Net Security
5 free resources from CISA #cybersecurity #ciso #cisa #opensource #tips #shorts
2 years ago - 0:21

Phoenix Security
#appsec #Protecting #Business #Operations #Reducing #Impact and Ensuring #businesscontinuity
1 year ago - 0:46

Wallarm
API Attacks Up 150% — Here’s Why You Should Care Now #APISecurity #APIAttacks #AIVulnerabilities
3 months ago - 0:47

Phoenix Security
Predicting Software Exploits Stay One Step Ahead with AI
1 year ago - 0:54

Phoenix Security
Discover the data for #vulnerability #exploit #prioritization #riskbased #applicationsecurity #cisa
1 year ago - 2:37

Phoenix Security
The #Microsoft #Security #Revolution From Terrible to Top in Remediation Speed
1 year ago - 0:49

Phoenix Security
#Boosting #Network #Security Faster #Remediation and #Painless #Code #fixes
1 year ago - 0:29

Phoenix Security
#Exploited #Vulnerability TOP 10 - The Dangers of #log4j The Most Exploited Software #reels #shorts
1 year ago - 0:17

Phoenix Security
Cybersecurity #Risk from #Vulnerability to #Business #Risk for for Effective Comms #cybersecurity
1 year ago - 0:55

Phoenix Security
#cisa #top12 #exploited #vulnerabilities the Most Exploited Security Vulnerabilities of 2022 S
1 year ago - 0:33
Phoenix Security
#Vulnerability #Exploitability #Shocking #Insights #Microsoft and Oracle Rank Highest #epss #shorts
1 year ago - 0:57

Security Daily Review
Actively Exploited: Commvault Web Shells, Active! mail RCE, and Brocade Code Injection Now in KEV
2 months ago - 17:21

BaseFortify
BaseFortify is your free, AI-powered Threat Intelligence platform built for modern security teams. Combining Deep Learning with ...
@BaseFortify subscribers

Phoenix Security
The Secret to Improving in #VulnerabilityManagement Revealed #epss
1 year ago - 0:37

Phoenix Security
The Key to Effective #Vulnerability #Fixes Providing #Context and Understanding #vulnerability
1 year ago - 0:40

Phoenix Security
#vulenrability #prioritization in #vulnerabilitymanagement and #applciationsecurity #shocking
1 year ago - 0:35

Dan Thorne
How to Use Tenable for CISA Vulnerability Alerts (Quick Tenable Explanation)
4 months ago - 2:47

TaroのIT
SAP NetWeaver .. etc. / KEV (Known Exploited Vulnerabilities) Catalog
3 years ago - 8:48

Phoenix Security
Unlocking Vulnerabilities The #Power of #SSVC #Decision #Trees for Faster Solutions
1 year ago - 0:48

Nucleus Security
June 9, 2023: A Week in Vulnerability Management with Patrick Garrity
2 years ago - 6:26

Phoenix Security
Unveiling the Key to Defending Against #Exploitation #epss #priority in Your org #cybersecurity
1 year ago - 0:55

Eclypsium
How To Detect AMI BMC Vulnerabilities (CVE 2024 54085) with Eclypsium
11 days ago - 8:21

VulnCheck
VulnCheck is the vulnerability intelligence company helping enterprises, government organizations, and cybersecurity vendors ...
@vulncheck subscribers

Phoenix Security
Uncovering #equifax #strut #Vulnerability #Exploit #Exposes #Legacy #Systems #vulnerability
1 year ago - 0:35

Phoenix Security
The #Microsoft #Security #Revolution From Terrible to Top in Remediation Speed
1 year ago - 0:49

Phoenix Security
#Exploitability in the Wild, What does it mean? #cybersecurity #vulnerabilitymanagement #exploits
1 year ago - 4:40

Skybox Security Demo Videos - Sean Keef
@SkyboxSecurityDemoVideos-SK subscribers

Phoenix Security
Boost your #productivity with #EPSS for effortless collaboration #priority #vulnerability #cyber
1 year ago - 0:17

Wallarm
AI Vulnerabilities Are API Vulnerabilities #APIsecurity #AIsecurity #Cybersecurity
2 months ago - 0:41

LOVI - Loginsoft Vulnerability Intelligence
Loginsoft Vulnerability Intelligence (LOVI) delivers real-time, actionable insights for enterprise organizations and security product ...
@LOVI-LoginsoftVulnerability subscribers

Phoenix Security
#Vulnerability #Exploitability #Shocking #Insights #Microsoft and Oracle Rank Highest #epss #shorts
1 year ago - 0:57

Phoenix Security
🚨 #Atlassian #Vulnerabilities Uncovered Critical #CVE-2023-22523, #CVE-2023-22524, #CVE-2023-22522
1 year ago - 2:06

Phoenix Security
The Hidden #Danger of #Scanning #Vulnerabilities in the #Cloud #cybersecurity
1 year ago - 0:57

Phoenix Security
on a #DATA with #Vulnerability #Exploitability, #prioritize #vulnerabilities #cybersecurity #data
1 year ago - 41:32

FedScoop
White House advances AI plans; CISA cites Ivanti bug risks | The Daily Scoop Podcast
9 months ago - 3:41

Nucleus Security
June 16, 2023: A Week in Vulnerability Management with Patrick Garrity
2 years ago - 11:22