
NetworkChuck
how Hackers SNiFF (capture) network traffic // MiTM attack
4 years ago - 19:07

Eye on Tech
What is a Man-in-the-Middle Attack? (In About A Minute)
3 years ago - 1:20

CertBros
ARP Poisoning | Man-in-the-Middle Attack
4 years ago - 11:35

VPNpro
Man-in-the-middle attack EXPLAINED: HOW can you to prevent MITM attack
4 years ago - 3:54

David Bombal
iPhone and Android WiFi Man-in-the-middle attack // PYTHON Scapy scripts for attacking networks
3 years ago - 15:24

TestOut LabSim
10.2.7 Perform an MITM Attack from a Remote Computer
2 years ago - 5:17

Robotics with Om Sir
Man-In-The-Middle Attack (MITM) Live Demonstration - Wi-Fi Hacks | Wireshark
2 years ago - 8:47

The Exploit Lab
Man-in-the-Middle Attack 40 Minutes Practical Tutorial | Step-by-Step Ethical Hacking
6 months ago - 40:46

Infosec
How to set up a man in the middle attack | Free Cyber Work Applied series
4 years ago - 11:54

The Linux Point
Kali Linux - Man In The Middle Attack (MITM) Tutorial Using Ettercap
4 years ago - 3:21

FR Mods
How to zanti app to MITM attack #mitm #acttak #rafithetechnologies
10 months ago - 1:01

FSOCIETY.COMMUNITY
How Man-in-the-Middle (MitM) Attacks Work #linux #mitmattack #cybersecurity #ethicalhacking
11 months ago - 0:16

Hasnain Dark Net
Man‑in‑the‑Middle (MITM) Attack DEMO – Intercept & Steal Login Credentials
12 days ago - 7:47

Nour's tech talk
Intercept and modify network traffic EASY MITM Attack (Bettercap tutorial)
3 years ago - 9:06

Loi Liang Yang
Get Usernames and Passwords with Ettercap, ARP Poisoning (Cybersecurity)
5 years ago - 6:53

Master Infosec
Hackers Use This Tool to Spy on Your Internet Traffic! #EthicalHacking #MITMAttack #NetworkSecurity
5 months ago - 1:16

SecurityFirstCorp
What Are The Signs Of A Man-in-the-Middle (MitM) Attack? - SecurityFirstCorp.com
4 months ago - 2:24

MMID BD to UK
Preventing Man in the Middle (MiTM) attack for securing Network
6 years ago - 3:35

CyberopSands
how Hackers SNiFF (capture) Passwords// MiTM attack
10 months ago - 0:32

GODLIKE JONATHAN
How to protect your PC against MITM attack? #shorts
4 years ago - 0:20

Ubuntu Maniac
Man in the Middle Attack MITM Using Wireshark and Ettercap | Full Tutorial For Beginner 2022
3 years ago - 7:10

Cyber Defentech
Ever heard of a Man-in-the-Middle (MITM) attack?
1 month ago - 0:25
Cyber3ra
What is Man in the middle (MITM) attack?
3 years ago - 0:28

Sean Choi
Mininet SSH MITM Attack Demo
9 years ago - 1:33

Douglas Fessler
EtterCap & Wireshark to do a MiTM attack (Proof of concept)
3 years ago - 8:01

CBT Nuggets
What is a Man-in-the-Middle Attack?
4 years ago - 5:52

Inno TechTips
MiTM Attack | ARP Spoofing | ARP Poisoning in Kali Linux
2 years ago - 8:18

Secure Well
How Hackers Steal Your Data: MiTM Attack Explained
6 months ago - 6:05

Dark Hacking Zone
MITM Attack Kya Hota Hai? 20 Second Mein Samjho! | #mitm #shorts #cybersecurity
10 days ago - 0:19

ScorpSec
MITM attack💀
2 years ago - 0:30

SecurityFirstCorp
What Is a Man-in-the-Middle (MITM) Attack? | SecurityFirstCorp News
8 months ago - 2:59

IT Developer
Bettercap ARP Spoofing🕵🏼Man In The Middle - MITM 15.2
2 years ago - 11:30

Cyber Guard
MITM Attack Explained In Hindi - Tutorial For Beginners
1 year ago - 7:57

TechVantage
Day 28: MITM Attack | #informationsecurity #tech #cybersecurity #ethicalhackinglearning
8 months ago - 0:34

Enicomp Media
How to Avoid Man in the Middle Attacks
4 months ago - 0:58

Cyberlearnix
Day 10 Animated MITM Attack #cyberattack #crypto #onlinesafety #cyberlearnix #chatgpt
3 weeks ago - 1:03

PUNEET DUBEY
man-in-the-middle (MITM) attacks #MITM #hacker #hack #hacking #shorts #short
1 year ago - 0:16

Cyber proctor
MITM ATTACK Explained in 38 seconds! #MITMAttack #ethical hacking #cyber attack
8 months ago - 0:39

SecurityFirstCorp
What Is An MITM Attack? - SecurityFirstCorp.com
7 months ago - 2:52

ESSE - RISE GmbH
DEMO: TLS KCI MitM Attack against Facebook (proof-of-concept)
9 years ago - 5:08

Jiffry Uthumalebbe
What is "Man-in-the-middle (MITM) attack"? | May 17, 2023
2 years ago - 2:49

From Code to Cosmos
Public Wi-Fi? Think Again.|| Man-in-the-Middle in 60 Seconds
3 months ago - 0:39

Yuvalearn
Cyber security agenda - 5 ) MITM Attack
3 years ago - 2:02

CISSP Study Group
MITM Attack - FREE CISSP Study Group - #shorts #cissp #education #cybersecurity
11 months ago - 0:29

Jiffry Uthumalebbe
What is "Man-in-the-middle (MITM) attack"? (In 28 Sec) | May 17, 2023
2 years ago - 0:28

CyberEncrypt
MITM Attack Explained in 40 Seconds 🔒
1 month ago - 0:41

Pyuthan IT ज्ञान 4.0
Biggest cyber attacks of all time #phishingattacks #cybersecurity #cyberattack #cybersports #cyber
1 year ago - 0:07

anonymous000$
Man in the middle attack (mitm) attack #hack #noobbhacker #mobilele #hackmon #prohacker #unhackable
6 months ago - 0:57

ThetechCrime
Hacking : MITM Attack #Hacking #MITMAttack #CyberSecurity #HindiTech
4 months ago - 0:53

0xShakhawat
MITM Attack Explained: Man-in-the-Middle Attack - 0xShakhawat
2 years ago - 1:16

iCSP A2B2
Is Someone Listening In on Your Conversations? Exploring MITM Attack Tactics #shortsvideo #shorts
1 year ago - 0:18

spiritual
Learn how hackers use MITM attack | Animated video
4 years ago - 3:27

Beyond the Cyber Wall
How ARP Spoofing Works in MITM Attack 🔥 Cyber Attack Explained in Simple Words
4 days ago - 0:55

Zilox
Bettercap2 Tutorial: MITM Attack Explained
1 year ago - 2:47

IT Developer
Bettercap ARP Spoofing🕵🏼Man In The Middle - MITM 15.2
2 years ago - 11:30

Majestro90
Kali Linux Tutorials - MITM Attack (Urlsnarf) #023
10 years ago - 4:32

I'M Hacker
Performing a MITM attack and hijack session using driftnet and urlsnarf #2022 #bestcourse #mitm
3 years ago - 6:29

Cyber Guard
MITM Attack Explained In Hindi - Tutorial For Beginners
1 year ago - 7:57

Connect APAC HK
MitM attack and How We Protect Your Mobile App?
5 years ago - 2:38

MaxYT
Prevent MITM Attack with Secure WiFi | #cybersecurity
1 year ago - 0:43

SecurityFirstCorp
What Steps Would You Take to Prevent an MITM Attack? | SecurityFirstCorp News
8 months ago - 3:34

ArchHacker
MITM Attack #attack #linux #coding #nmap #ping #website #tools #website #scanning #virus #python
4 months ago - 0:42

ArchHacker
Wire Shark MITM Attack #attack #linux #shark #hacker #tools #nmap
2 months ago - 0:16
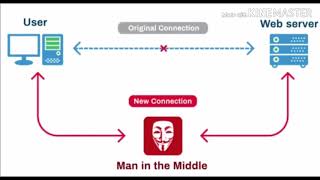
Cyberist
MITM Attack explained
5 years ago - 1:57

SKILL SHIFT
MITM ATTACK || what is MITM attack
2 years ago - 0:43

CYBER HEAL
Russian Hackers Exploit RDP Proxies for MiTM Attacks! #Cybersecurity #Hackers #RDPProxy #MiTMAttacks
7 months ago - 0:55

Cyber proctor
MITM ATTACK Explained in 38 seconds! #MITMAttack #ethical hacking #cyber attack
8 months ago - 0:39

Perisai Cybersecurity
☕ Logging into your bank account on café Wi-Fi like it’s a safe space?
2 months ago - 0:55

Archives Of A Coding Student
Man-in-the-Middle (MitM) Attack #codingtutorial #educational #hacking101 #cyberattack #cybersecurity
6 days ago - 0:44
Robomart
MITM Attack on Local Server
9 years ago - 9:01

SKILL SHIFT
What Is MITM Attack? #hacking
2 years ago - 0:49

Techinsights
I Hacked Him With a MITM Attack
5 months ago - 2:03

MIT-LEARNING
Certified Ethical Hacker (CEH) v12 - Performing an MITM Attack with Ettercap
10 months ago - 10:47

BleepingComputer
MiTM attack in APT Linux Package Manager Demo
6 years ago - 0:34

Inno TechTips
MiTM Attack | ARP Spoofing | ARP Poisoning in Kali Linux
2 years ago - 8:18

ZoneAlarm
MitM attack Demo
3 years ago - 2:14

N45HT
How Hackers Steal YOUR DATA Without You Noticing #MiTM Attack #ShawnRyan #RyanMontgomery #0day
1 year ago - 1:01

Babul Raj
What is M.I.T.M attack?
3 years ago - 0:59

Excel@FIT
26 - Automation of MitM Attack on WiFi Networks (Martin Vondráček)
8 years ago - 1:00

Cyber Hub
Man in the middle (Mitm) attack
11 months ago - 0:44

LEX1000
MiTM Attack
3 months ago - 0:16
The Secure Programmer
How Hackers Exploit Public Wi-Fi | MITM Attack Explained & Prevention Tips #hackers
4 months ago - 0:47

Shield Identity
Protecting against man-in-the-middle (MITM) attacks.
3 weeks ago - 0:56

Ak hacking_8
Wireshark MITM Attack 🔥 Learn How Hackers Steal Your D__#ethical #computersecurity #ethicalhacking
4 months ago - 0:44

Hatacoyama
MITM Attack Demo (MASSIVE)
7 months ago - 1:00

RivØlta
ARP Spoofing - MiTM Attack, Combined With Urlsnarf & Driftnet
3 years ago - 2:39

CYB3R
When you try to send data securely, but a hacker snatches it mid-transfer... | Meme #shorts
5 months ago - 0:05

Axximum Infosolutions
MITM Attack Explained – How Hackers Steal Your Data! #cybersecurity #ethicalhacking #MITMAttack
5 months ago - 0:50

Cyber Raj
What Is MITM ATTACK #shorts #cybersecurity #securityengineer
1 month ago - 0:52

Cyber XS
MITM Attack | Bettercap #cyberxs #hacking #bettercap
4 months ago - 0:26

LearnWithRookie
Quiz #20 protocol vulnerable to MitM Attack #shorts #shortsfeed #comptiasecurity #wireless #viral
2 years ago - 0:31

VPNRanks
The Secret App That Could Ruin Google Pixel!
11 months ago - 0:54
![MITM Attack Explained: How Hackers Steal Your Data in 2025 [Live Demo] #hacker #cybersecurity #data](/vi/czFc51RRe8M/mqdefault.jpg)
Saurabh Kokate
MITM Attack Explained: How Hackers Steal Your Data in 2025 [Live Demo] #hacker #cybersecurity #data
5 months ago - 0:36

Mavisec
Perform MITM Attack with Ettercap | ARP Poisoning
3 years ago - 1:43













































































































![MITM Attack Explained: How Hackers Steal Your Data in 2025 [Live Demo] #hacker #cybersecurity #data](/vi/czFc51RRe8M/mqdefault.jpg)
