
The Cyber Mentor
What is Broken Access Control? A Quick Guide for Beginners
7 months ago - 12:04

Rana Khalil
Broken Access Control | Complete Guide
2 years ago - 39:33

Vooki Infosec
What is A01 - 2021 Broken Access Control? #BrokenAccessControl #OWASPTop10BrokenAccessControl
1 year ago - 4:40

BePractical
Broken Access Control Explained: How to Discover It in 2025?
4 months ago - 9:23

Aikido Security
Broken Access Control Explained: OWASP Top 10 A01 Explained with Examples
10 months ago - 7:04

Indusface
What is Broken Access Control?
2 months ago - 1:52

security content
Broken Access Control and Preventions #owasp #owasptop10 #brokenaccesscontrol #cybersecurity
1 year ago - 5:17

Ryan John
Hacking Websites | Broken Access Control
2 years ago - 12:42

ARABSECLAB
Broken access control attack LAB شرح ثغره
3 years ago - 1:29:34

pentestTV
Broken Access Control: Hacking the OWASP Top 10
4 months ago - 8:05

Vooki Infosec
OWASP TOP 10 - 2017 : Broken Access Control #owasptop10 #BrokenAccessControl
1 year ago - 3:07

Martin Voelk
Broken Access Control Vulnerabilities | FirstBlood v1 | Bug Bounty Service
2 years ago - 5:38

Exploits Simplified
$1,000 Broken Access Control Insecure Direct Object References-IDOR | Bug Bounty 2023 | Bugcrowd VRT
4 years ago - 1:04

Redfox Security
Exploiting Broken Access Control | Web Application Pentesting
9 months ago - 0:54

Aikido Security
Broken Access Control TLDR - OWASP #1 vuln in 60 seconds
10 months ago - 1:00

Redfox Security
Web App Access Control Secrets Revealed!
9 months ago - 0:25

George
Broken Access control
4 years ago - 5:36

Encrypticsecurity
Top Cybersecurity Expert Reveals Broken Access Control Secrets
10 months ago - 0:46

InsiderPhD
"Easiest" Beginner Bugs? Access Control and IDORs
2 years ago - 31:46

Göktuğ Ekinci
WebGoat (A1) Broken Access Control: Hijack a Session Demo
3 months ago - 7:38

zSecurity
Broken Access control, what it is and why it is important.
11 months ago - 1:00

Hackdoor
A5 Broken Access Control Forced Browsing OWASP Juice Shop Tutorial OWASP Top Ten
5 years ago - 3:35

Security For You
Broken Access Control - Top 10 Vulnerabilities 🚨 Watch full video on @security_for_you👇🔗 #shorts 80
1 year ago - 1:01

Redfox Security
Explaining Broken Access Control | What is broken access control | Redfox Security #podcast
1 year ago - 0:57

SafeOps
Understanding Broken Access Control: OWASP Top 10 Vulnerabilities Explained
8 months ago - 1:36

cyber phisher
What is Broken Access Control ? |A Major Web Security Threat|The Danger of Broken Access Control |
2 months ago - 0:40

VZsecure Class
Broken Access Control - Getting Admin Panel on Website..
2 years ago - 1:19

security content
Broken Access Control #cybersecurity #owasp #owasptop10 #brokenaccesscontrol #vapt
1 year ago - 0:49

mona explains security
Broken Access Control - Privilege Escalation | Beginner's Guide to Web Security #3
2 years ago - 16:21

Hackdoor
A5 Broken Access Control OWASP Juice Shop Challenge - OWASP Top Ten Tutorial
5 years ago - 3:15

Ubaid Ahmed
Security Testing: Broken Access Control | Part 8
2 years ago - 15:19

Hackitron
Broken Access Control: A Common Security Weakness You Need to Know About
2 years ago - 2:26

HowToPega
OWASP Top 1 Vulnerability 2021: "Broken Access Control"
2 years ago - 26:30
![OWASP Top 10: Broken Access Control [1/10]](/vi/0Zi3rUdEomg/mqdefault.jpg)
Dune Security
OWASP Top 10: Broken Access Control [1/10]
3 months ago - 1:26

Maisam Noyan
Broken Access Control Explained in Less than 1-Minute #accesscontrol #shorts
2 years ago - 0:59

DEVIL HACKS IT
Broken Access Control Vulnerability Explained Bug Biryani Day 10 #bughunting #bugbounty #securitybug
3 months ago - 0:40

Semi Yulianto
Tips and Tricks: Broken Access Control (Bug Bounty Approach)
1 year ago - 6:10
![[Hindi] Broken Access Control | OWASP Top 10](/vi/zNhfQuDUeLU/mqdefault.jpg)
Ethical Sharmaji
[Hindi] Broken Access Control | OWASP Top 10
2 years ago - 3:02

cyber phisher
How to Prevent Broken Access Control | Best Practices
2 months ago - 0:38

RaviTeja Mureboina
Broken Access Control #shorts #owasp #owasptop10 #accesscontrol #websecurity #cybersecurity
1 year ago - 0:26

Hax Kitten
Unlocking the Secrets of Broken Access Control The Flag Challenge #tryhackme #cybersecurity
1 year ago - 0:24

Cyber Bark LLC
🔓 OWASP Top 10: Broken Access Control — When Anyone Can Be Admin || @CyberBarkLLC || IT Services
1 month ago - 1:01

Muskan Singh
Broken Access Control #coding #owasptop10 #brokenaccesscontrolexplained #htmlcss #overthewire
1 year ago - 1:00

Pluralsight
Secure Coding Skills: Preventing Broken Access Control Course Preview
5 years ago - 1:43

Cyber Samir
Broken Access Control (A Critical Security Vulnerability)
4 months ago - 1:37

VISTA InfoSec
Broken Access Control | OWASP TOP 10
1 year ago - 18:09

CodeMake
broken access control vulnerability explanation and examples
1 month ago - 1:33

FullProxy Labs
F5 WAF vs OWASP #5 Broken Access Control
6 years ago - 3:47

Cybertix
Broken Access Control
1 year ago - 0:31

CyberTodd
Broken Access Control (IDOR Challenge) | Answer the Questions Series #shorts #thm #tryhackme
11 months ago - 0:45

Whoami Security
Broken Access Control - Exploiting broken access control to escalate privileges
3 years ago - 4:22

CodeRift
how to find broken access control vulnerabilities in
1 month ago - 1:10

SecurityFirstCorp
What Is Broken Access Control? - SecurityFirstCorp.com
5 months ago - 3:36

CyberSec365
"OWASP Top 10: Broken Access Control Explained & How to Mitigate It"
1 year ago - 7:54

Vooki Infosec
Examples of Broken Access Control and how to prevent them #shorts
1 year ago - 0:50

Evolua
🔐 Broken Access Control: A Simple Path to Data Leaks #shorts #security
6 months ago - 1:30

Rana Khalil
Broken Access Control - Lab #1 Unprotected admin functionality | Long Version
2 years ago - 16:33

WHITE HACK LABS
Exploiting Broken Access Control (part2) #shorts #cybersecurity #ethicalhacking
6 months ago - 1:01
![[Hindi] Broken Access Control | OWASP Top 10](/vi/zNhfQuDUeLU/mqdefault.jpg)
Ethical Sharmaji
[Hindi] Broken Access Control | OWASP Top 10
2 years ago - 3:02

Hack Sphere X
Can Hackers EXPLOIT Broken Access Control? – Lec 70
6 months ago - 1:18

Redfox Security
Broken Access Control: The Weak Link in Web Security | Web Application Pentesting
9 months ago - 0:23

ARABSECLAB
Broken access control attack LAB شرح ثغره
3 years ago - 1:29:34

Travis Yeargan
ThreatBee Wordpress Plugin Simple 301 Critical Alert
4 years ago - 0:56

OliveStem
An Introduction to OWASP Top 10 Vulnerabilities - Broken Access Control
2 years ago - 7:14

Need to explore
How Token Manipulation Leads to Broken Access Control | Ethical Hacking
4 months ago - 1:52

AppSec Zeroed
Introduction to Broken Access Control | OWASP Top 10
7 months ago - 1:23

RootHunter
OWASP Top 10 2017 | A5: Broken Access Control
5 years ago - 2:17

Raúl Piracés (piraces)
Broken Access Control - Fixed Vulnerability w/ protection against enumeration
2 years ago - 1:17

Mokshit KalRa
Broken Access Control of Admin panel - Bypass POC - Weak Web | By Mokshit Kalra |
4 years ago - 1:05

RAD Security
Access Control Design: Fixing Broken Access Control
1 year ago - 18:11

Claranet UK
OWASP Top 10: Broken Access Control
4 years ago - 7:53

SecurityFirstCorp
What Is Broken Access Control In Cybersecurity? - SecurityFirstCorp.com
8 months ago - 2:18

CodeFix
Broken access control explained
4 months ago - 15:48

Osprey Tango
LESSON 14: Implementing RBAC to Address Broken Access Control Issues in Web Applications
11 months ago - 0:41

CodeMake
broken access control understanding and exploiting access
1 month ago - 1:35

z3nsh3ll
Broken Access Control - User ID Controlled By Request Parameter
1 year ago - 5:20

Faisal Fs
Broken Access Control
4 years ago - 2:44

Raúl Piracés (piraces)
Broken Access Control - Enumeration attack w/ no authorization guards
2 years ago - 1:38

CodeMake
broken access control how to prevent owasp
1 month ago - 1:22

Obscure
Day5OWASP Top 10 | Day 5 Broken Access Control | part 2 complete | Tryhackme | walk-through
5 years ago - 4:51

PseudoTime
Owasp Top 10 - Broken Access Control
5 years ago - 1:22

CypherX
Broken Access Control!! ₹ #cybersecurity #hacker # shorts
1 year ago - 0:30
![Broken Access Control [Practical Explanation]](/vi/7DmNpLymVw8/mqdefault.jpg)
Hacker_Apple
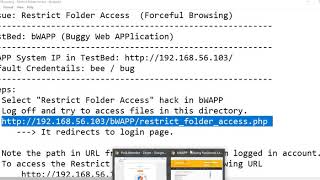
Broken Access Control [Practical Explanation]
11 months ago - 3:19

CodeMake
broken access control attack examples and 4 defensive measures
1 month ago - 1:21

SecurIT360
OWASP Top 10: 1 - Broken Access Control
3 years ago - 3:30

EvonSys MSP
#OWASP Awareness 2023 - Broken Access Control Guidelines - - EvonSys MSP Video Series - 5/10
1 year ago - 3:15

z3nsh3ll
Broken Access Control - User ID Controlled by Request Parameter with Unpredictable User IDs
1 year ago - 7:22

Decrypt3r
OWASP Top 10 - Broken Access Control(IDOR) on Try Hack Me | OWASP Top 10 THM Walkthrough | Decrypt3r
4 years ago - 4:19

Evolua
Broken Access Control: A Simple Path to Data Leaks
6 months ago - 1:49

ZeroTrust Zone
Broken Access Control| Part 2 #shorts
1 month ago - 0:30

WHITE HACK LABS
Hijacking the Family Tree: Exploiting Broken Access Control #shorts #ethicalhacking #cybersecurity
6 months ago - 1:01

WEB - MICH JOSH CYBERSECURITY
🌐"𝐖𝐄𝐁 𝐏𝐄𝐍𝐓𝐄𝐒𝐓𝐈𝐍𝐆 -𝐉𝐔𝐈𝐂𝐄 𝐒𝐇𝐎𝐏 𝐇𝐨𝐰 𝐁𝐫𝐨𝐤𝐞𝐧 𝐀𝐜𝐜𝐞𝐬𝐬 𝐂𝐨𝐧𝐭𝐫𝐨𝐥 𝐋𝐞𝐭𝐬 𝐘𝐨𝐮 𝐀𝐜𝐜𝐞𝐬𝐬 𝐭𝐡𝐞 𝐀𝐝𝐦𝐢𝐧 𝐏𝐚𝐧𝐞𝐥 𝐢𝐧 𝐉𝐮𝐢𝐜𝐞 𝐒𝐡𝐨𝐩
3 months ago - 1:48

VISTA InfoSec
Broken Access Control Vulnerability
1 month ago - 9:02

Cyberwings Security
Broken Access Control and IDOR Vulnerabilities: A Practical Guide with Try Hack Me Labs in Hindi
1 year ago - 21:21

CodeMind
Broken access control explained how to discover it in 2025
2 months ago - 42:10

10 Minutes Hack
🔐A01: Broken Access Control | 🛠️ Practice ENG
1 month ago - 11:15

10 Minutes Hack
🔐 A01: Broken Access Control | 🧾 Summary ENG
1 month ago - 0:58

CyberTodd
Broken Access Control | Answer the Questions Series #shorts #thm #tryhackme
11 months ago - 0:25

anonymousdevilsec
Broken Access Control Vulnerability! | OWASP Top 10
2 years ago - 1:11

hawkwheels
OWASP Broken Access Control | OWASP top - 1 Room walkthrough
1 year ago - 36:52

Lim Jet Wee
Cyber Security - Broken Access Control
4 years ago - 7:10

z3nsh3ll
Broken Access Control - User ID Controlled by Request Parameter with Password Disclosure
1 year ago - 5:08

Hackerjedi
Broken Access Control Vulnerability | Portswigger lab-1 to lab-4
1 year ago - 9:41

AppSec Zeroed
Broken Access Control Part 1 | Admin Access Labs | Hidden URLs | Role Manipulation Exploits
6 months ago - 9:07

Mr Cyberian
What Is Access Control & Broken Access Control - தமிழ் || Mr Cyberian
1 year ago - 3:34

Codecrypts Academy
IDOR POC | Broken Access Control #idor #burpsuite #cybersecurity #hacker #bugbountytip #bugbounty
3 weeks ago - 1:37

CodeGen
Bugcrowd university broken access control testing
4 months ago - 19:20

TheBlaineBot
Cybersecurity for Web Developers - OWASP Top 10: #5 Broken Access Control
4 years ago - 8:28

Redfox Security
The Hidden Dangers of Broken Access Control
6 months ago - 0:21

z3nsh3ll
Unprotected Admin Functionality - Broken Access Control
2 years ago - 4:16

The Cyber Athlete
Full Penetration Test (Unguided) | Broken Access Control - HTB Oopsie
1 year ago - 1:14:05

Cybersecurity Tutorials
Broken Access Control #owasp #owasptop10 #applicationsecurity #webapplicationsecurity #pentesting
2 years ago - 0:16

TheShield BugBounty
The Shield Bug Bounty Thursday "Broken Access Control Vulnerabilities"
3 years ago - 1:13:32

Hackers Adda
Owasp Top 10 tryhackme Broken Access Control | Broken Access Control Tryhackme | hackersadda
4 years ago - 5:11

Hacker Vlog
#1 Broken Access Control 😲 | bug hunting for beginners | bug bounty for beginners| hacker vlog live
Streamed 2 years ago - 1:39:20

N2K Networks
OWASP broken access control (noun)
2 months ago - 7:45











































![OWASP Top 10: Broken Access Control [1/10]](/vi/0Zi3rUdEomg/mqdefault.jpg)


![[Hindi] Broken Access Control | OWASP Top 10](/vi/zNhfQuDUeLU/mqdefault.jpg)



















































![Broken Access Control [Practical Explanation]](/vi/7DmNpLymVw8/mqdefault.jpg)








































